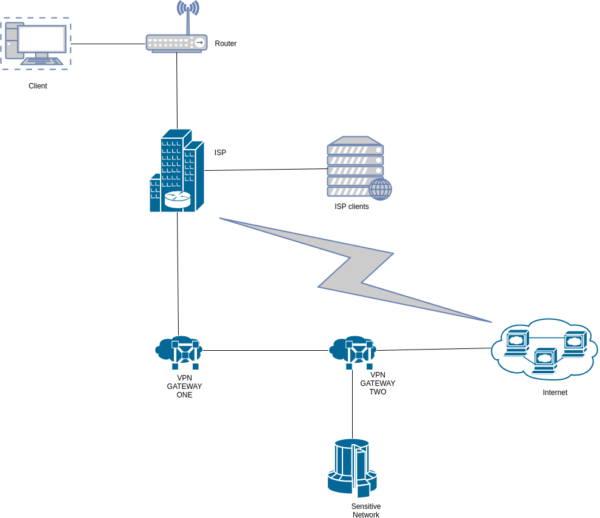
Understanding Chaining VPNs
Chaining VPNs, also known as cascading VPNs or VPN cascades, involve routing internet traffic through multiple VPN servers in succession. This technique adds layers of encryption and anonymity, enhancing online security and privacy for users. By chaining VPNs, users can obscure their digital footprint further, making it challenging for third parties to track their online activities.
Exploring the Dynamics of Chaining VPNs
Chaining VPNs operates by establishing a connection to one VPN server, which then routes the traffic to another VPN server before reaching the final destination. Each VPN server in the chain encrypts and decrypts data, thereby adding an extra layer of security. This process makes it exceedingly difficult for adversaries to intercept and decipher the transmitted data.
Key Features of Chaining VPNs
- Enhanced Security: Chaining VPNs increases security by encrypting data multiple times, making it highly resistant to interception.
- Improved Anonymity: With each VPN server in the chain, the user’s IP address gets masked, enhancing anonymity and thwarting attempts to trace online activities.
- Geographical Flexibility: Users can choose VPN servers located in different countries, allowing them to bypass geo-restrictions and access region-locked content.
- Traffic Obfuscation: Chaining VPNs makes it harder for ISPs and government agencies to monitor and throttle internet traffic, ensuring greater freedom and privacy online.
Types of Chaining VPNs
There are various approaches to chaining VPNs, each offering unique advantages and considerations. Here are some common types:
| Type | Description |
|---|---|
| Serial Cascade | In a serial cascade, each VPN server forwards traffic to the next VPN server in the chain, creating a linear sequence of encrypted connections. |
| Parallel Cascade | Parallel cascades involve splitting the internet traffic into multiple streams, each routed through a different VPN server simultaneously for added security. |
| Mixed Cascade | Mixed cascades combine elements of serial and parallel cascades, offering a blend of enhanced security and optimized performance. |
Ways to Utilize Chaining VPNs
- Enhanced Privacy: Chaining VPNs can be used to bolster privacy by obscuring online activities from ISPs, government surveillance, and malicious actors.
- Access Restricted Content: Users can bypass censorship and access geo-blocked content by connecting to VPN servers located in unrestricted regions.
- Secure Remote Access: Chaining VPNs can facilitate secure remote access to corporate networks and sensitive data, safeguarding confidential information from interception.
Challenges and Solutions
Despite their benefits, chaining VPNs may encounter challenges such as reduced connection speeds and increased latency. These issues can be mitigated through:
- Optimized Server Selection: Choosing VPN servers with minimal latency and sufficient bandwidth can alleviate speed-related concerns.
- Bandwidth Management: Implementing bandwidth management techniques helps prioritize critical traffic and optimize resource utilization.
- Regular Maintenance: Performing regular maintenance and updates on VPN infrastructure ensures optimal performance and security.
Main Characteristics and Comparisons
| Characteristic | Chaining VPNs | Traditional VPNs |
|---|---|---|
| Security | High | Moderate |
| Anonymity | Enhanced | Limited |
| Complexity | Moderate | Low |
| Performance | Variable | Consistent |
Future Perspectives and Technologies
The future of chaining VPNs holds promise for advancements in encryption protocols, network optimization, and user-friendly interfaces. Emerging technologies such as decentralized VPNs (dVPN) and blockchain-based solutions offer decentralized and censorship-resistant alternatives to traditional VPN services.
Integration with VPN Services
Chaining VPNs can be seamlessly integrated with existing VPN services, allowing users to enhance their security and privacy without sacrificing convenience. Many VPN providers offer built-in support for chaining VPNs, simplifying the setup process for users.
Resources for Further Information
For those interested in delving deeper into the world of chaining VPNs, the following resources provide valuable insights and guidance:
- “The Ultimate Guide to Chaining VPNs” – [Link]
- “Cascading VPNs: An In-Depth Analysis” – [Link]
- “Chaining VPNs: Best Practices and Considerations” – [Link]
By leveraging chaining VPNs, users can fortify their online defenses and reclaim control over their digital privacy and security. With careful consideration of the challenges and benefits, individuals can harness the power of VPN cascades to navigate the internet with confidence and peace of mind.