Cryptography serves as the cornerstone of secure communication and data protection in the digital age. By leveraging mathematical principles and algorithms, cryptography enables the transformation of information into a format that is unintelligible to unauthorized parties. This article delves into the intricacies of cryptography, exploring its key features, types, applications, challenges, and future prospects, as well as its synergy with VPN technology.
Understanding Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of adversaries. It encompasses various methods for encoding and decoding information to ensure confidentiality, integrity, authentication, and non-repudiation. At its core, cryptography relies on complex mathematical algorithms to encrypt plaintext into ciphertext and vice versa, making it indecipherable to anyone lacking the appropriate decryption key.
Exploring Cryptography in Depth
Cryptography encompasses a wide array of concepts, including symmetric and asymmetric encryption, hash functions, digital signatures, and cryptographic protocols. These components play crucial roles in securing data transmission, verifying the authenticity of messages, and safeguarding sensitive information from unauthorized access or tampering.
Key Features of Cryptography
| Feature | Description |
|---|---|
| Confidentiality | Ensures that data remains private and cannot be accessed by unauthorized parties. |
| Integrity | Guarantees that data remains unchanged and unaltered during transmission. |
| Authentication | Verifies the identity of communicating parties, preventing impersonation or fraud. |
| Non-repudiation | Prevents parties from denying their involvement in a transaction or communication. |
Types of Cryptography
Cryptography can be categorized into several types based on the techniques and algorithms employed:
-
Symmetric Cryptography: Utilizes a single shared key for both encryption and decryption, offering fast processing speeds and simplicity. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
-
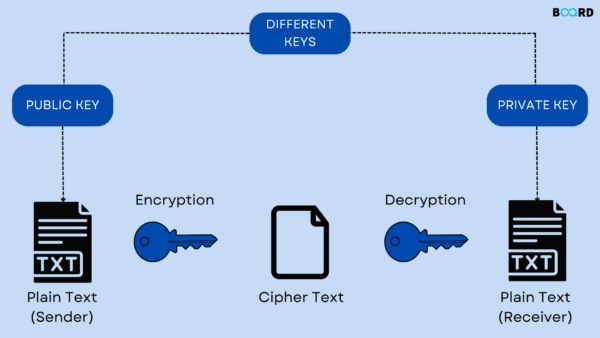
Asymmetric Cryptography: Employs a pair of keys—a public key for encryption and a private key for decryption. This enables secure communication without the need to exchange secret keys beforehand. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are popular asymmetric encryption schemes.
-
Hash Functions: Transform input data into a fixed-size string of bytes, known as a hash value or digest. Hash functions are crucial for data integrity verification and password hashing. Common algorithms include SHA-256 (Secure Hash Algorithm) and MD5 (Message Digest Algorithm 5).
Applications of Cryptography
Cryptography finds extensive application across various domains, including:
- Secure Communication: Protects emails, instant messages, and online transactions from eavesdropping and interception.
- Data Encryption: Safeguards sensitive information stored on computers, mobile devices, and cloud servers.
- Digital Signatures: Validates the authenticity and integrity of electronic documents, contracts, and transactions.
- Blockchain Technology: Secures decentralized ledgers and cryptocurrencies through cryptographic hashing and digital signatures.
Challenges and Solutions
Despite its efficacy, cryptography is not without challenges. Common issues include key management, algorithm vulnerabilities, and quantum computing threats. To address these concerns, ongoing research focuses on developing quantum-resistant algorithms, enhancing key distribution mechanisms, and bolstering cryptographic protocols against emerging threats.
Comparisons and Characteristics
| Term | Description |
|---|---|
| Cryptography vs. Steganography | Cryptography hides information through encryption, while steganography conceals data within other media. |
| Cryptography vs. Cryptology | Cryptography specifically deals with secure communication techniques, whereas cryptology encompasses the broader study of codes and ciphers. |
Future Perspectives
The future of cryptography is poised for significant advancements, driven by emerging technologies such as quantum computing, homomorphic encryption, and post-quantum cryptography. These innovations hold the promise of enhancing security, privacy, and resilience in the digital realm.
Cryptography and VPN
Virtual Private Networks (VPNs) leverage cryptographic techniques to create secure, encrypted tunnels for transmitting data over public networks. By encrypting internet traffic and masking users’ IP addresses, VPNs provide enhanced privacy, security, and anonymity online. Cryptography ensures that data exchanged between VPN clients and servers remains confidential and protected from interception by malicious actors.
Resources for Further Exploration
For those interested in delving deeper into the realm of cryptography, the following resources offer valuable insights and information:
- National Institute of Standards and Technology (NIST) – Cryptographic Standards and Guidelines: link
- International Association for Cryptologic Research (IACR) – Cryptography Resources: link
- Cryptography and Network Security: Principles and Practice by William Stallings (Publisher: Pearson)
In conclusion, cryptography stands as an indispensable tool for securing digital communication, protecting sensitive data, and upholding privacy in an increasingly interconnected world. Through ongoing research and innovation, the field continues to evolve, driving advancements in cybersecurity and shaping the future of secure communication technologies.