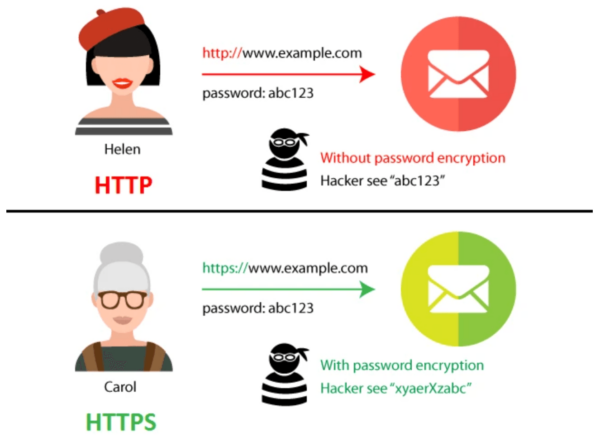
HTTPS (Hypertext Transfer Protocol Secure) is a communication protocol used for secure data transmission over the internet. It is an extension of the Hypertext Transfer Protocol (HTTP), but with an added layer of encryption provided by Transport Layer Security (TLS) or its predecessor, Secure Sockets Layer (SSL). This encryption ensures that data exchanged between the client (such as a web browser) and the server remains private and cannot be easily intercepted or tampered with by malicious actors.
Detailed Information about HTTPS (Hypertext Transfer Protocol Secure)
HTTPS works by encrypting data using cryptographic algorithms, making it unreadable to anyone who doesn’t have the appropriate decryption key. This encryption process occurs during the initial handshake between the client and server, where they agree on a cipher suite and exchange cryptographic keys. Once the secure connection is established, data can be safely transmitted between the two parties.
One of the primary goals of HTTPS is to provide authentication, ensuring that the client is communicating with the intended server and not an imposter. This is achieved through the use of digital certificates, which are issued by trusted third-party Certificate Authorities (CAs). These certificates contain information about the server’s identity and are used to verify its authenticity.
Detailed Analysis of the Key Features of HTTPS (Hypertext Transfer Protocol Secure)
Key features of HTTPS include:
- Encryption: All data transmitted between the client and server is encrypted, protecting it from eavesdropping and tampering.
- Authentication: HTTPS verifies the identity of the server, preventing man-in-the-middle attacks and ensuring the integrity of the communication.
- Data Integrity: HTTPS ensures that data remains unchanged during transmission, preventing unauthorized modification.
- Trust: HTTPS relies on trusted Certificate Authorities to issue digital certificates, establishing trust in the identity of the server.
Types of HTTPS (Hypertext Transfer Protocol Secure)
HTTPS primarily exists in two forms:
| Type | Description |
|---|---|
| Standard HTTPS | Utilizes the TLS or SSL protocol to encrypt data exchanged between the client and server. |
| Extended Validation (EV) HTTPS | Provides a higher level of assurance by conducting more rigorous validation of the server’s identity. |
Ways to Use HTTPS (Hypertext Transfer Protocol Secure)
HTTPS is commonly used in various scenarios, including:
- Secure browsing of websites, ensuring privacy and security for users.
- Secure transmission of sensitive information, such as login credentials, financial data, and personal details.
- Secure communication between web applications and servers, protecting data exchanged in real-time.
Problems Arising with the Use of HTTPS (Hypertext Transfer Protocol Secure) and Their Solutions
Some challenges associated with HTTPS include:
- Performance overhead due to encryption and decryption processes.
- Compatibility issues with older web browsers and servers.
- Costs associated with obtaining and maintaining SSL/TLS certificates.
These issues can be addressed through:
- Optimization techniques to mitigate performance overhead.
- Regular updates and patches to ensure compatibility.
- Adoption of free or low-cost SSL/TLS certificate options, such as Let’s Encrypt.
Main Characteristics and Comparisons with Similar Terms
| Characteristic | HTTPS | HTTP |
|---|---|---|
| Encryption | Yes | No |
| Authentication | Yes | No |
| Data Integrity | Yes | No |
| Secure Data Transmission | Yes | No |
Perspectives and Technologies of the Future Related to HTTPS (Hypertext Transfer Protocol Secure)
Future advancements in HTTPS may include:
- Continued improvements in encryption algorithms and protocols to enhance security.
- Integration with emerging technologies such as quantum encryption for even stronger protection against threats.
- Increased automation and simplification of certificate management processes.
How VPN Can Be Used or Associated with HTTPS (Hypertext Transfer Protocol Secure)
VPN services can complement HTTPS by providing an additional layer of privacy and security. By encrypting all internet traffic at the network level, VPNs ensure that data remains secure even before it reaches the HTTPS layer. This combination of VPN and HTTPS offers users enhanced protection against surveillance, censorship, and cyber threats.
Links to Resources for More Information about HTTPS (Hypertext Transfer Protocol Secure)
For more information about HTTPS and related topics, you can refer to the following resources:
- “HTTPS explained” by Mozilla: https://developer.mozilla.org/en-US/docs/Web/HTTP/Overview
- “SSL/TLS Strong Encryption: How It Works” by SSL.com: https://www.ssl.com/faqs/ssl-tls-encryption/
- “Let’s Encrypt – Free SSL/TLS Certificates” by Let’s Encrypt: https://letsencrypt.org/
These resources provide comprehensive explanations, tutorials, and best practices for implementing and managing HTTPS in various contexts.