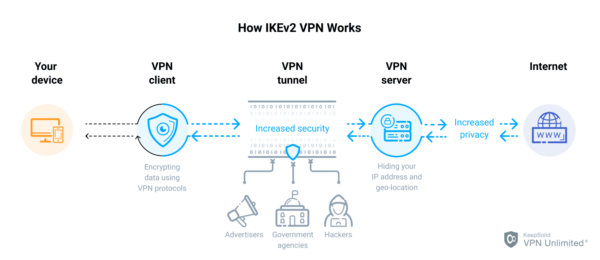
IKEv2, short for Internet Key Exchange version 2, is a protocol used in the creation of Virtual Private Networks (VPNs) to establish and manage secure connections. It serves as a key component in the negotiation of security associations (SAs) and the exchange of cryptographic keys between two parties, typically a client device and a VPN server. IKEv2 is designed to provide high levels of security, efficiency, and flexibility in VPN deployments, making it a popular choice among both enterprises and individual users.
Overview of IKEv2
IKEv2 was standardized in RFC 5996 and introduced as an enhancement to its predecessor, IKEv1. It offers several improvements over IKEv1, including better resilience to network changes, faster connection establishment, and support for mobility and multi-homing. IKEv2 is primarily used in conjunction with IPsec (Internet Protocol Security) for securing communication channels over the internet.
Key Features of IKEv2
IKEv2 boasts several key features that make it a preferred protocol for VPN implementations:
-
Efficiency: IKEv2 is optimized for quick connection setup, minimizing latency and providing seamless roaming capabilities for mobile devices.
-
Resilience: It can quickly re-establish connections in the event of network disruptions, ensuring uninterrupted VPN access.
-
Mobility Support: IKEv2 supports seamless handovers between different networks, making it ideal for users who frequently switch between Wi-Fi, cellular, or other connection types.
-
Enhanced Security: The protocol offers strong cryptographic algorithms for securing data transmission, ensuring confidentiality, integrity, and authenticity of VPN traffic.
-
NAT Traversal: IKEv2 includes built-in support for NAT traversal, allowing VPN traffic to pass through network address translation devices without requiring additional configuration.
Types of IKEv2
IKEv2 can be classified into different types based on various criteria, including authentication methods, encryption algorithms, and key exchange modes. The following table provides an overview of common types of IKEv2 configurations:
| Type | Description |
|---|---|
| IKEv2 Main Mode | Traditional mode of IKEv2 negotiation with multiple steps |
| IKEv2 Aggressive Mode | A simplified mode of negotiation, requiring fewer exchanges |
| IKEv2 with Pre-Shared Key | Authentication based on a pre-shared secret |
| IKEv2 with Digital Certificates | Authentication using X.509 certificates |
Uses of IKEv2
IKEv2 can be utilized in various scenarios and applications, including:
- Secure remote access for telecommuters and mobile workers.
- Site-to-site VPN connections between geographically dispersed offices.
- Secure communication for IoT (Internet of Things) devices and industrial control systems.
- VPN services for personal privacy and online anonymity.
Challenges and Solutions
Despite its many benefits, IKEv2 implementation may encounter challenges such as:
- Compatibility issues with legacy systems or devices.
- Potential vulnerabilities in outdated cryptographic algorithms.
- Configuration complexity, especially for advanced deployment scenarios.
To address these challenges, organizations can adopt best practices such as:
- Regularly updating VPN software and firmware to ensure compatibility and security.
- Implementing strong encryption and authentication mechanisms.
- Employing centralized management tools for streamlined configuration and monitoring.
Characteristics and Comparisons
The following table compares IKEv2 with other VPN protocols in terms of key characteristics:
| Protocol | Key Characteristics |
|---|---|
| IKEv2 | Efficient, resilient, supports mobility, strong security |
| OpenVPN | Highly configurable, open-source, cross-platform |
| L2TP/IPsec | Widely supported, easy to configure, moderate security |
| WireGuard | Lightweight, modern cryptography, experimental |
Future Perspectives
Looking ahead, the future of IKEv2 is likely to involve:
- Continued optimization for emerging technologies such as 5G networks and IoT devices.
- Integration with advanced security mechanisms such as post-quantum cryptography.
- Standardization efforts to address evolving threats and regulatory requirements.
VPN and IKEv2
IKEv2 plays a crucial role in the operation of VPN services, enabling secure and reliable communication between clients and servers. By utilizing IKEv2, VPN providers can offer users enhanced privacy, data protection, and access to geo-restricted content.
Additional Resources
For more information about IKEv2 and VPN technologies, consider exploring the following resources:
- RFC 5996: Internet Key Exchange Protocol Version 2 (IKEv2)
- Internet Engineering Task Force (IETF) Working Group on IPsec
- VPN Protocol Comparison: IKEv2 vs. OpenVPN vs. L2TP/IPsec vs. WireGuard
This comprehensive overview of IKEv2 highlights its significance in the realm of VPN technology, its features and implementations, challenges, and future prospects.