Brief Information about Key Exchange
Key exchange is a crucial aspect of secure communication protocols, including those used in Virtual Private Network (VPN) services. It involves the secure exchange of cryptographic keys between parties to enable encrypted communication and protect data from unauthorized access.
Detailed Information about Key Exchange
Key exchange mechanisms establish a shared secret key between communicating parties without revealing it to potential eavesdroppers. This process typically involves cryptographic algorithms and protocols designed to ensure confidentiality, integrity, and authenticity of exchanged keys. In the context of VPNs, key exchange protocols play a vital role in establishing secure tunnels between users and VPN servers, safeguarding sensitive information from interception or manipulation.
Detailed Analysis of the Key Features of Key Exchange
Key exchange protocols should possess several key features to ensure the security of communication channels:
- Confidentiality: Keys exchanged should remain secret to unauthorized parties.
- Integrity: Keys should not be tampered with during transmission.
- Authentication: Parties involved should verify each other’s identities to prevent impersonation attacks.
- Forward Secrecy: Even if a long-term key is compromised, past communications remain secure.
- Efficiency: Key exchange should be computationally feasible and not introduce significant overhead.
Types of Key Exchange
Various key exchange mechanisms exist, each with its strengths and weaknesses. Some common types include:
| Key Exchange Type | Description |
|---|---|
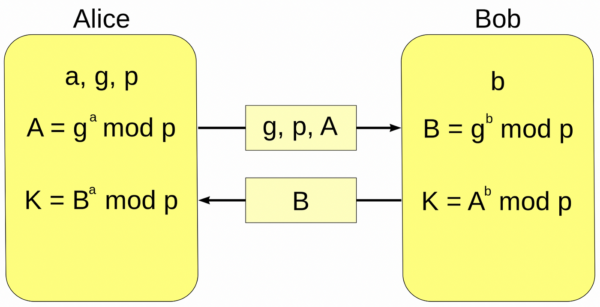
| Diffie-Hellman | Allows two parties to generate a shared secret key over an insecure channel without prior keys. |
| RSA Key Exchange | Utilizes asymmetric encryption for key exchange, relying on the difficulty of factoring large primes. |
| Elliptic Curve Diffie-Hellman (ECDH) | Variant of Diffie-Hellman using elliptic curve cryptography for improved efficiency. |
Ways to Use Key Exchange
Key exchange protocols are integral to various applications, including:
- Secure Communication: Enabling encrypted communication channels in VPNs, secure messaging apps, and online banking.
- Secure Access Control: Facilitating secure authentication and access control in networked systems and IoT devices.
- Digital Signatures: Supporting the generation and verification of digital signatures to ensure data integrity and authenticity.
Problems and Solutions with Key Exchange
Despite their importance, key exchange protocols face challenges such as:
- Man-in-the-Middle Attacks: Adversaries intercepting and modifying exchanged keys.
- Key Management: Securely storing and updating keys to prevent unauthorized access.
- Quantum Threats: Future quantum computers could break existing cryptographic algorithms.
These issues can be mitigated through measures like using authenticated key exchange protocols, employing robust key management practices, and researching quantum-resistant cryptography.
Main Characteristics and Comparisons
Key Exchange vs. Public Key Infrastructure (PKI):
| Characteristic | Key Exchange | PKI |
|---|---|---|
| Key Management | Shared secret keys | Public/private key pairs |
| Scalability | May require additional overhead for key distribution | Supports large-scale deployments with certificate authorities |
| Authentication | Relies on shared secrets and authentication protocols | Utilizes digital certificates for identity verification |
Perspectives and Future Technologies
As technology evolves, key exchange protocols will continue to evolve to address emerging threats and requirements. Future trends in key exchange include:
- Post-Quantum Cryptography: Developing cryptographic algorithms resistant to quantum attacks.
- Blockchain-based Key Management: Leveraging blockchain technology for secure and decentralized key management.
- Homomorphic Encryption: Enabling computations on encrypted data without decryption, enhancing privacy in key exchange.
VPN and Key Exchange
VPNs heavily rely on key exchange protocols to establish secure connections between users and VPN servers. Key exchange ensures that data transmitted over VPN tunnels remains confidential and protected from unauthorized access. By integrating robust key exchange mechanisms, VPN services can offer enhanced security and privacy to users, safeguarding their online activities from potential threats.
Links to Resources
For more information about key exchange and related topics, refer to the following resources:
- NIST Special Publication 800-56A: Recommendation for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography
- RFC 2631: Diffie-Hellman Key Agreement Method
- Elliptic Curve Cryptography: a Gentle Introduction
- Post-Quantum Cryptography: NIST Standardization Process
This comprehensive guide provides insights into the importance, mechanisms, and future prospects of key exchange in ensuring secure communication, particularly in the realm of VPN services.