Brief Information about Malware:
Malware, short for malicious software, refers to any software specifically designed to disrupt, damage, or gain unauthorized access to computer systems, networks, or devices. It encompasses a wide range of malicious programs, including viruses, worms, Trojans, ransomware, spyware, adware, and more. Malware poses a significant threat to cybersecurity and can lead to data breaches, financial loss, and identity theft.
Detailed Information about Malware: Expanding the Topic:
Malware is a constant and evolving threat in the digital age, with cybercriminals continuously developing new techniques to bypass security measures and exploit vulnerabilities. It can be distributed through various vectors, such as email attachments, malicious websites, infected removable media, and compromised software. Once installed on a system, malware can execute a variety of malicious activities, including stealing sensitive information, encrypting files for ransom, hijacking computing resources for cryptocurrency mining, and remotely controlling infected devices.
Detailed Analysis of the Key Features of Malware:
Key features of malware include stealth, persistence, and versatility. Many malware variants are designed to operate stealthily, avoiding detection by antivirus software and other security mechanisms. They often employ techniques such as encryption, polymorphism, and rootkit capabilities to evade detection and removal. Additionally, malware can establish persistence on infected systems, ensuring that it remains active even after system reboots or antivirus scans. Moreover, malware is highly versatile, with attackers constantly innovating and adapting their tactics to exploit emerging vulnerabilities and security weaknesses.
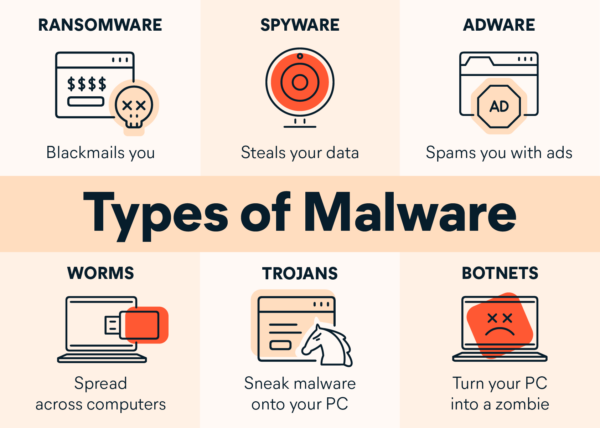
Types of Malware:
Malware comes in various forms, each with its own characteristics and methods of operation. Some common types of malware include:
| Type | Description |
|---|---|
| Virus | A type of malware that spreads by infecting files and replicating itself when executed. |
| Worm | A standalone malware program that self-replicates and spreads across networks, often exploiting vulnerabilities in operating systems and software. |
| Trojan Horse | Malicious software disguised as legitimate programs to trick users into executing them, allowing attackers to gain unauthorized access to systems or steal data. |
| Ransomware | Malware that encrypts files or locks users out of their systems, demanding payment (usually in cryptocurrency) for decryption or restoration of access. |
| Spyware | Malware designed to secretly monitor and collect information about users’ activities, such as browsing habits, keystrokes, and login credentials. |
| Adware | Software that automatically displays or downloads advertisements, often without the user’s consent, and may also track user behavior for targeted advertising. |
Ways to Use Malware:
Cybercriminals use malware for various malicious purposes, including:
- Stealing sensitive information, such as credit card numbers, passwords, and personal data.
- Disrupting critical infrastructure, such as power grids, telecommunications networks, and financial systems.
- Extorting money from individuals and organizations through ransomware attacks.
- Conducting espionage and surveillance for political, economic, or military purposes.
- Distributing spam emails, phishing scams, and other forms of social engineering attacks.
Problems and Solutions with Malware:
The use of malware presents several challenges for individuals, businesses, and cybersecurity professionals. Some common problems associated with malware include:
- Data breaches and financial losses resulting from stolen or compromised information.
- Disruption of business operations and loss of productivity due to malware-induced system downtime.
- Damage to reputation and trust in affected organizations, leading to customer attrition and revenue loss.
- Legal and regulatory consequences, including fines, penalties, and lawsuits for non-compliance with data protection laws.
To mitigate the risks associated with malware, individuals and organizations can implement a multi-layered approach to cybersecurity, including:
- Installing and regularly updating antivirus and antimalware software to detect and remove malicious threats.
- Implementing robust security measures, such as firewalls, intrusion detection systems, and data encryption, to protect against unauthorized access and data breaches.
- Educating users about cybersecurity best practices, such as avoiding suspicious email attachments, clicking on unknown links, and downloading software from untrusted sources.
- Backing up critical data regularly and storing backups in secure, offsite locations to facilitate recovery in the event of a ransomware attack or data loss incident.
Main Characteristics and Comparisons with Similar Terms:
To differentiate between malware and similar terms:
| Term | Definition |
|---|---|
| Malware | Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems, networks, or devices. |
| Virus | A type of malware that spreads by infecting files and replicating itself when executed. |
| Worm | A standalone malware program that self-replicates and spreads across networks, often exploiting vulnerabilities in operating systems. |
| Trojan Horse | Malicious software disguised as legitimate programs to trick users into executing them, allowing attackers to gain unauthorized access. |
| Ransomware | Malware that encrypts files or locks users out of their systems, demanding payment for decryption or restoration of access. |
| Spyware | Malware designed to secretly monitor and collect information about users’ activities without their knowledge or consent. |
| Adware | Software that displays advertisements and may track user behavior for targeted advertising, often bundled with free software downloads. |
Perspectives and Future Technologies Related to Malware:
As technology continues to evolve, so too will the techniques and tactics used by cybercriminals to develop and distribute malware. Future trends and technologies related to malware may include:
- Artificial intelligence and machine learning algorithms to enhance malware detection and classification capabilities.
- Blockchain technology to improve the security and integrity of digital transactions and prevent tampering with malware distribution channels.
- Quantum cryptography to develop unbreakable encryption methods and secure communication protocols against quantum computing-enabled attacks.
- Collaborative efforts between governments, law enforcement agencies, and cybersecurity vendors to combat cybercrime and disrupt malware operations on a global scale.
VPN and its Association with Malware:
Virtual Private Networks (VPNs) play a crucial role in mitigating the risks associated with malware by encrypting internet traffic and providing secure connections to remote networks. VPNs can help protect against man-in-the-middle attacks, data interception, and eavesdropping by encrypting data transmissions between users and VPN servers. Additionally, VPNs can bypass geographic restrictions and censorship imposed by governments or internet service providers, enabling users to access restricted content and websites securely.
By routing internet traffic through encrypted tunnels, VPNs can prevent malicious actors from intercepting sensitive information or injecting malware into unsecured connections. Moreover, VPNs offer anonymity and privacy protection by masking users’ IP addresses and encrypting their online activities, making it harder for cybercriminals to track and trace their digital footprints.
However, it’s essential to choose a reputable VPN provider that prioritizes user privacy and security, as some free or low-cost VPN services may compromise user data or engage in questionable practices, such as logging user activity or selling user information to third parties. FineVPN, as a free VPN service, prioritizes user privacy and security, offering encrypted connections, no-logs policy, and reliable server infrastructure to protect against malware and other cyber threats.
Links to Resources for More Information about Malware:
For more information about malware and cybersecurity best practices, please refer to the following resources:
- National Institute of Standards and Technology (NIST) – NIST provides comprehensive guidelines