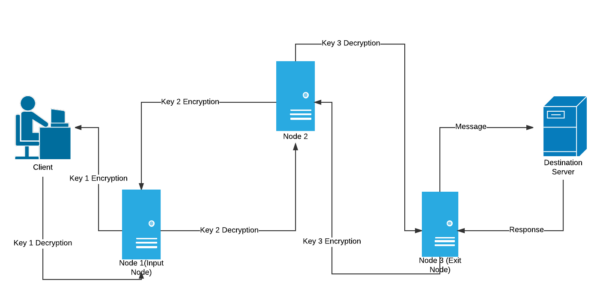
Onion Routing is a sophisticated method for anonymous communication over a computer network. In this technique, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, with each one peeling away a single layer of encryption to reveal the data’s next destination. By the time the message reaches its final recipient, all layers of encryption have been removed, ensuring the original message is delivered securely and privately.
The Fundamentals of Onion Routing
Onion Routing was developed in the mid-1990s by Paul Syverson, Michael G. Reed, and David Goldschlag at the Naval Research Laboratory. The primary aim was to protect the privacy and security of U.S. intelligence communications online. This technology forms the basis of the Tor network, which is widely used for anonymous web browsing and protection against traffic analysis.
Onion Routing’s core principle involves encrypting messages multiple times and sending them through a network of routers. Each router decrypts only enough to know the next destination, with the final layer of encryption being removed by the recipient. This process ensures that no single point in the network knows both the origin and the destination of the data, providing anonymity to the users.
Key Features of Onion Routing
Onion Routing’s architecture provides several unique features:
- Anonymity: It conceals the user’s identity and online activity from surveillance and traffic analysis by separating identification and routing information.
- Security: Multiple layers of encryption ensure that intercepted traffic at any point in the network is indecipherable.
- Resistance to Censorship: By hiding the user’s location and usage, it allows for the circumvention of geolocation-based censorship and content restrictions.
Varieties of Onion Routing
| Type | Description | Use Case |
|---|---|---|
| Traditional Onion Routing | The original form, using a predetermined sequence of routers. | Basic anonymous communication. |
| Tor (The Onion Router) | An advanced system that builds upon the original concept with improved security features. | Secure web browsing, confidential communications. |
| Garlic Routing | A variant that bundles multiple messages together to further obfuscate the communication. | Used in I2P (Invisible Internet Project) for enhanced anonymity. |
Applications of Onion Routing
Onion Routing can be utilized in various ways, including:
- Private Web Browsing: Protecting users’ identities while accessing the internet.
- Secure Communication: Offering a platform for encrypted messaging and email services.
- Circumvention of Censorship: Enabling access to restricted content and services in oppressive regimes.
- Whistleblowing: Providing a safe channel for whistleblowers to share sensitive information.
Challenges and Solutions in Onion Routing
Despite its advantages, Onion Routing faces several challenges:
- Performance: The layered encryption and rerouting can cause significant latency. Solution: Implementing more efficient routing algorithms and encryption methods.
- Security Vulnerabilities: Potential attacks on the network can compromise anonymity. Solution: Continuous updates and security patches, along with research into new encryption techniques.
- Legal and Ethical Issues: Misuse for illegal activities poses ethical dilemmas. Solution: Law enforcement collaboration, without compromising user privacy, and public awareness campaigns.
Comparative Analysis with Similar Technologies
| Feature | Onion Routing | VPN (Virtual Private Network) | HTTPS |
|---|---|---|---|
| Anonymity | High | Medium | Low |
| Encryption | Multi-layer | Single-layer | End-to-end |
| Speed | Slower due to routing | Faster | Fast |
| Use Case | Anonymity, security | Remote access, privacy | Secure transactions |
Future Directions in Onion Routing Technology
Future advancements in Onion Routing include:
- Quantum-resistant encryption: Ensuring security against quantum computing threats.
- Improved routing efficiency: Reducing latency without compromising anonymity.
- Integration with blockchain: For decentralized trust mechanisms and enhanced privacy.
Integrating VPN with Onion Routing
A VPN can complement Onion Routing by providing an initial encryption layer, thus masking the entry point into the onion network. This setup can offer enhanced privacy and security, especially in environments where accessing the onion network directly might be monitored or restricted.
Further Reading and Resources
For more in-depth information on Onion Routing, consider these authoritative sources:
- The Tor Project: https://www.torproject.org/
- Naval Research Laboratory Onion Routing Archive: https://www.onion-router.net/
- Electronic Frontier Foundation (EFF) on Anonymity Online: https://www.eff.org/issues/anonymity
This comprehensive guide to Onion Routing underscores its significance in the modern digital landscape, offering a potent tool for privacy, security, and freedom online. Through continuous development and responsible use, Onion Routing remains at the forefront