Brief Information about Proxy
A proxy server, commonly referred to as a proxy, acts as an intermediary between a user and the internet. It facilitates requests from clients seeking resources from servers, providing various benefits such as enhanced privacy, security, and access to geo-blocked content.
Detailed Information about Proxy
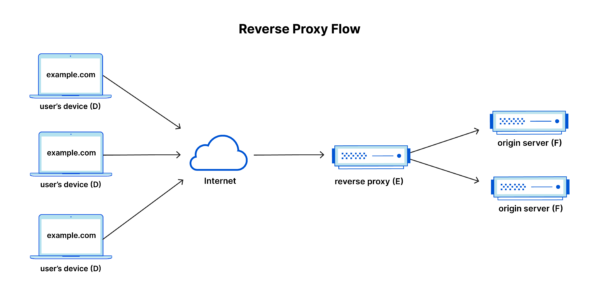
Proxy servers intercept requests from users and forward them to the desired destination, serving as a middleman in the communication process. They operate by receiving requests from clients, such as web browsers or applications, and relaying them to the internet on behalf of the client. The response from the internet is then sent back to the proxy server, which forwards it to the client. This process effectively hides the client’s IP address and location from the internet server, enhancing privacy and anonymity.
Detailed Analysis of the Key Features of Proxy
Proxy servers offer several key features, including:
- Anonymity: Proxies conceal the user’s IP address, making it difficult for websites to track their online activities.
- Content Filtering: Proxies can be configured to block access to certain websites or content categories, providing content filtering and censorship bypassing capabilities.
- Bandwidth Savings: By caching frequently accessed resources, proxies can reduce bandwidth usage and improve network performance.
- Access Control: Proxies enable administrators to control access to the internet by restricting or allowing access based on predefined rules or policies.
- Security: Proxies can serve as a barrier between internal networks and the internet, offering an additional layer of security by inspecting and filtering incoming and outgoing traffic for malicious content.
Types of Proxy
Proxy servers come in various types, each offering distinct functionalities and use cases. The most common types of proxies include:
| Proxy Type | Description |
|---|---|
| HTTP Proxy | Handles HTTP traffic and is commonly used for web browsing. Suitable for accessing web content and bypassing internet censorship. |
| HTTPS Proxy | Similar to HTTP proxies but with added encryption for secure communication. Ideal for accessing sensitive information and protecting data transmitted over the internet. |
| SOCKS Proxy | Supports multiple protocols and is often used for non-web traffic such as email, gaming, and file sharing. Offers greater flexibility and compatibility with various applications. |
| Transparent Proxy | Intercept and redirect traffic without requiring any configuration on the client-side. Often used in corporate networks for monitoring and controlling internet usage. |
| Residential Proxy | Utilizes IP addresses assigned to residential ISPs, providing a higher level of anonymity and reducing the likelihood of detection by websites employing IP blocking techniques. |
Ways to Use Proxy
Proxy servers find application in various scenarios, including:
- Accessing Blocked Content: Proxies enable users to bypass geo-restrictions and access content that is otherwise unavailable in their region.
- Enhancing Privacy: By masking the user’s IP address, proxies help protect privacy and anonymity online, preventing websites and advertisers from tracking user activities.
- Improving Security: Proxies can act as a barrier against cyber threats by filtering malicious content and preventing direct access to internal networks from external sources.
- Speeding up Web Browsing: Caching proxies store frequently accessed web content, reducing load times and bandwidth usage for subsequent requests.
Problems Arising with the Use of Proxy and Solutions
While proxy servers offer numerous benefits, they may also encounter challenges such as:
- Slow Performance: Overloaded or improperly configured proxies can result in slow browsing speeds. This issue can be mitigated by optimizing proxy settings and deploying additional resources to handle increased traffic.
- Security Risks: Unsecured proxies may expose users to security vulnerabilities, such as man-in-the-middle attacks or data breaches. Implementing encryption protocols and regularly updating proxy software can help mitigate these risks.
- Compatibility Issues: Certain applications or websites may not function correctly when accessed through a proxy server due to compatibility issues or restrictive filtering policies. Users can address this by configuring proxy settings or using alternative proxy solutions.
Main Characteristics and Comparisons with Similar Terms
| Feature | Proxy | VPN |
|---|---|---|
| Encryption | Optional | Mandatory |
| Anonymity | Moderate to High | High |
| Traffic Routing | Application-specific | System-wide |
| Security | Limited | High |
| Performance | Variable | Consistently High |
| Cost | Often Free | Paid |
Perspectives and Future Technologies Related to Proxy
The future of proxy technology is characterized by advancements in:
- Machine Learning: Proxies leveraging machine learning algorithms can better detect and prevent emerging threats, enhancing security and threat intelligence capabilities.
- Edge Computing: Proxies deployed at the network edge can improve latency and performance by caching content closer to end-users, supporting the growing demand for real-time applications and services.
- Blockchain Integration: Blockchain-based proxies offer decentralized and transparent network infrastructure, enhancing trust, privacy, and censorship resistance in the proxy ecosystem.
How VPN Can be Used or Associated with Proxy
Virtual Private Networks (VPNs) often complement proxy servers, providing additional layers of security and privacy. While proxies primarily route specific types of traffic, such as HTTP or SOCKS, VPNs encrypt all internet traffic, ensuring end-to-end privacy and security. By combining VPNs with proxies, users can enjoy enhanced anonymity, access to geo-restricted content, and improved security posture.
Links to Resources for More Information about Proxy
For further information on proxy servers and related technologies, consider exploring the following resources:
- Mozilla Developer Network: Proxy Server
- TechTarget: Proxy Server
- Cloudflare: What is a Proxy Server?
- OpenVPN: Understanding VPNs and Proxy Servers
These resources offer valuable insights into the functionality, implementation, and best practices associated with proxy servers and their integration with other networking technologies.