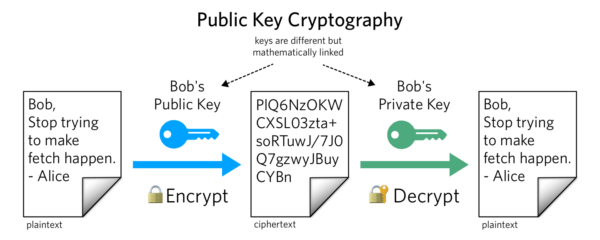
Brief Information about Public Key:
Public key cryptography, also known as asymmetric cryptography, is a foundational concept in modern cybersecurity. It revolves around the use of two keys, a public key and a private key, to encrypt and decrypt data securely. The public key is freely available to anyone and is used for encryption, while the private key is kept secret and is used for decryption. This system enables secure communication and data exchange over insecure networks like the internet.
Detailed Information about Public Key:
Public key cryptography relies on mathematical algorithms to generate pairs of keys. The public key is derived from the private key, but it is computationally infeasible to reverse-engineer the private key from the public key. This asymmetry forms the basis of the security of the system. When a sender wants to send a secure message to a recipient, they use the recipient’s public key to encrypt the message. Only the recipient, who possesses the corresponding private key, can decrypt and access the original message.
Detailed Analysis of the Key Features of Public Key:
- Security: Public key cryptography provides strong security guarantees, even in the presence of adversaries attempting to intercept or tamper with communications.
- Authentication: Public key infrastructure (PKI) enables entities to verify the authenticity of digital signatures and certificates, ensuring trust in online transactions and communications.
- Key Exchange: Public key algorithms facilitate secure key exchange protocols like Diffie-Hellman, enabling parties to establish shared secret keys over insecure channels.
- Digital Signatures: Public key cryptography enables the creation and verification of digital signatures, which are used to authenticate the origin and integrity of digital documents and messages.
Types of Public Key:
There are several types of public key algorithms, each with its own strengths and weaknesses. Some common types include:
| Algorithm | Description |
|---|---|
| RSA | Named after its inventors, Rivest, Shamir, and Adleman, RSA is widely used for encryption, digital signatures, and key exchange. |
| Elliptic Curve Cryptography (ECC) | ECC offers comparable security to RSA but with smaller key sizes, making it more efficient for resource-constrained environments such as mobile devices and IoT devices. |
| Diffie-Hellman | Although not strictly a public key algorithm, Diffie-Hellman key exchange is a foundational protocol for securely establishing shared secret keys between parties. |
Ways to Use Public Key:
- Secure Communication: Public key cryptography enables secure communication channels for transmitting sensitive information, such as financial transactions, personal messages, and business data.
- Data Encryption: Public key encryption is used to protect data at rest and in transit, ensuring confidentiality and privacy.
- Digital Signatures: Public key digital signatures are employed to authenticate the origin and integrity of digital documents, ensuring non-repudiation and trustworthiness.
- Key Management: Public key infrastructure (PKI) facilitates the management of cryptographic keys, including generation, distribution, revocation, and renewal.
Problems and Solutions with the Use of Public Key:
Problems:
- Key Management: Managing a large number of cryptographic keys securely can be challenging, particularly in distributed systems.
- Key Distribution: Ensuring the secure distribution of public keys to authorized parties without interception or tampering poses a significant challenge.
- Performance Overhead: Public key operations can be computationally intensive, leading to performance overhead, especially in high-volume systems.
Solutions:
- Key Rotation: Regularly rotating cryptographic keys and certificates helps mitigate the risk of key compromise and improves overall security.
- Certificate Authorities (CAs): Utilizing trusted CAs for issuing and validating digital certificates enhances the trustworthiness of public key infrastructure.
- Hardware Security Modules (HSMs): Employing HSMs for key storage and cryptographic operations enhances the security of sensitive key material.
Main Characteristics and Comparisons:
| Characteristic | Public Key | Symmetric Key |
|---|---|---|
| Key Distribution | Publicly available | Pre-shared or distributed |
| Key Length | Typically longer | Shorter |
| Performance | Computationally intensive | Efficient |
| Applications | Secure communication, digital signatures | Bulk data encryption, session key establishment |
Perspectives and Future Technologies:
- Post-Quantum Cryptography: Research is ongoing to develop cryptographic algorithms resilient to quantum computing threats, ensuring long-term security in the face of advancing technology.
- Homomorphic Encryption: Advances in homomorphic encryption enable computations on encrypted data without decryption, opening new possibilities for privacy-preserving computation in cloud environments.
- Blockchain and Distributed Ledger Technology (DLT): Integrating public key cryptography with blockchain and DLT enhances the security and trustworthiness of decentralized systems and digital assets.
VPN and Public Key:
Virtual Private Networks (VPNs) often utilize public key cryptography to secure communication between clients and servers. VPN protocols like OpenVPN and IPsec leverage public key algorithms for key exchange and authentication, ensuring confidentiality, integrity, and authenticity of VPN traffic over public networks.
Links to Resources:
- RSA Cryptography
- Elliptic Curve Cryptography
- Diffie-Hellman Key Exchange
- Public Key Infrastructure (PKI)
This comprehensive overview of public key cryptography demonstrates its pivotal role in securing modern communication systems and highlights its applications in various domains, including cybersecurity, finance, and digital identity management. For further exploration, the provided links offer additional insights and resources on the topic.