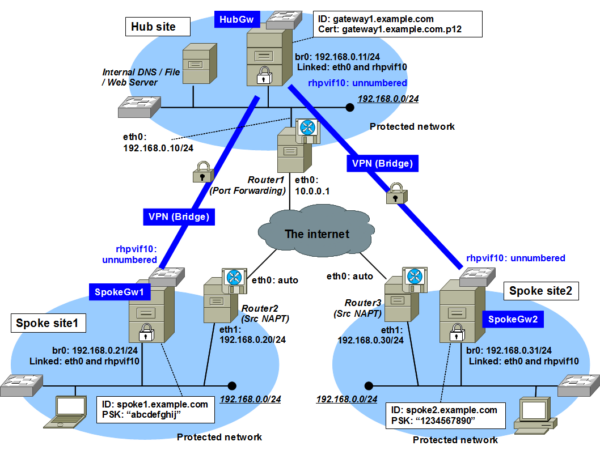
VPN Bridge is a pivotal technology in the world of virtual private networks (VPN), enabling the extension of a VPN over multiple network segments. This guide explores the concept of VPN Bridge, its key features, types, applications, potential issues, and its future outlook, providing a thorough understanding for both novices and experts alike.
Understanding VPN Bridge
A VPN Bridge connects two or more LAN segments over the internet, allowing them to function as a single network. Unlike traditional VPNs, which connect individual devices to a network, a VPN Bridge links entire networks, facilitating seamless communication between devices on different local networks as if they were on the same LAN.
Key Features of VPN Bridge
The key features of VPN Bridge include:
- Network Integration: Seamlessly integrates separate LANs into a single network.
- Security: Utilizes encryption protocols to secure data transmissions across public networks.
- Scalability: Easily expands to include more network segments without significant infrastructure changes.
- Flexibility: Supports various network protocols and topologies, making it adaptable to diverse networking environments.
Types of VPN Bridge
| Type | Description | Use Case |
|---|---|---|
| Layer 2 Bridge | Operates at the data link layer, forwarding traffic based on MAC addresses. | Ideal for extending broadcast domains across the internet. |
| Layer 3 Bridge | Operates at the network layer, routing traffic based on IP addresses. | Suitable for connecting distinct IP networks over a VPN. |
Applications of VPN Bridge
VPN Bridge finds application in various scenarios, including:
- Remote Work: Connects home networks to corporate LANs, enabling remote access to resources.
- Business Expansion: Links the networks of geographically dispersed offices, creating a unified corporate network.
- Education: Facilitates the integration of campus networks, allowing students and faculty to access resources from any location.
Challenges and Solutions in VPN Bridge Usage
The use of VPN Bridge can present challenges such as:
- Complex Configuration: Setting up a VPN Bridge can be technically challenging.
- Solution: Comprehensive documentation and user-friendly setup tools can simplify the process.
- Performance Bottlenecks: High traffic volumes can strain the VPN connection.
- Solution: Upgrading bandwidth and optimizing network configurations can alleviate congestion.
VPN Bridge Compared to Similar Technologies
| Feature | VPN Bridge | Standard VPN | Direct Connection |
|---|---|---|---|
| Scope | Connects networks | Connects individual devices to a network | Physical link between networks |
| Security | High (encryption) | High (encryption) | Varies |
| Flexibility | High | Medium | Low |
| Cost | Variable | Low | High (infrastructure) |
Future Perspectives and Technologies of VPN Bridge
The future of VPN Bridge is likely to be shaped by advancements in:
- Software-Defined Networking (SDN): Enhancing flexibility and control over network resources.
- Cloud Integration: Facilitating the creation of hybrid clouds by connecting on-premises networks to cloud services.
- Encryption Technologies: Improving security with more robust and efficient encryption algorithms.
VPN and VPN Bridge: A Synergistic Relationship
While a standard VPN focuses on connecting individual clients to a network, VPN Bridge extends this capability to entire networks. This synergy allows organizations to leverage the strengths of both technologies, offering secure, scalable, and flexible networking solutions.
Further Reading and Resources
For those seeking more in-depth information on VPN Bridge, the following resources are invaluable:
- IEEE Xplore: Scholarly articles on networking technologies, including VPN Bridge.
- RFCs (Request for Comments): Technical documents from the IETF that detail VPN protocols and implementations.
- Vendor Documentation: Specific guides and manuals provided by VPN solution vendors offer insights into proprietary implementations and best practices.
This comprehensive guide to VPN Bridge offers a deep dive into a technology that is reshaping the landscape of network connectivity and security. By understanding its features, applications, and future directions, organizations can better harness its potential to meet their networking needs.