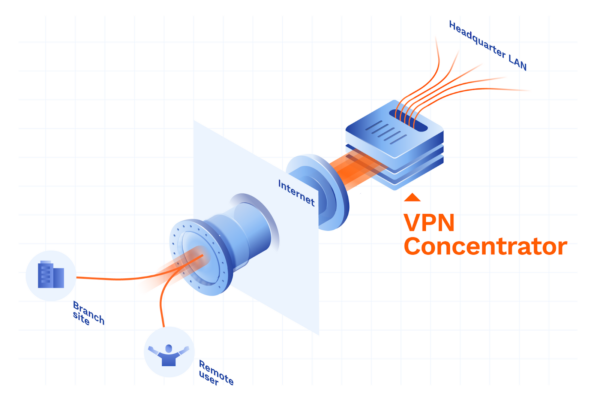
Brief Information about VPN Concentrator
A VPN concentrator, also known as a VPN gateway or VPN server, is a networking device that facilitates secure remote access to a private network across a public network such as the internet. It acts as a central point for managing multiple VPN connections and encrypting/decrypting data to ensure secure communication between remote users and the private network.
Detailed Information about VPN Concentrator
A VPN concentrator plays a crucial role in providing secure connectivity for remote users, branch offices, or partners accessing resources within a corporate network. It typically combines the functions of a firewall, VPN server, and authentication mechanism to ensure secure and reliable communication over the internet.
Key Features of VPN Concentrator
- Secure Tunneling: Utilizes various encryption protocols such as IPSec, SSL/TLS, or L2TP/IPSec to create secure tunnels for data transmission.
- Scalability: Supports a large number of simultaneous VPN connections, making it suitable for enterprises with diverse remote access needs.
- Authentication: Implements robust authentication mechanisms such as username/password, digital certificates, or two-factor authentication to verify the identity of remote users.
- Traffic Management: Prioritizes and manages VPN traffic to ensure optimal performance and bandwidth utilization.
- High Availability: Incorporates redundancy and failover mechanisms to minimize downtime and ensure uninterrupted connectivity.
- Logging and Monitoring: Provides comprehensive logging and monitoring capabilities to track VPN usage, detect anomalies, and troubleshoot issues effectively.
Types of VPN Concentrator
VPN concentrators can be classified based on their deployment and functionality:
| Type | Description |
|---|---|
| Hardware Appliance | Dedicated hardware devices designed specifically for VPN concentrator functionality. |
| Software-Based | Software applications or virtual appliances that can be installed on standard server hardware. |
Ways to Use VPN Concentrator
VPN concentrators find extensive use in various scenarios, including:
- Remote Access: Enabling remote employees to securely access corporate resources from anywhere.
- Branch Connectivity: Connecting branch offices or remote sites to a centralized network securely.
- Partner Collaboration: Facilitating secure communication and collaboration with external partners or vendors.
- Mobile Device Access: Providing secure access to internal resources for mobile devices such as smartphones and tablets.
Problems and Solutions with VPN Concentrator
Challenges with VPN concentrators may include:
- Scalability Issues: Addressed by implementing load balancing and scaling techniques to accommodate growing numbers of VPN connections.
- Performance Bottlenecks: Mitigated through hardware upgrades, optimization of encryption algorithms, and network optimization.
- Security Vulnerabilities: Managed by regularly updating firmware/software, implementing strong encryption protocols, and enforcing access control policies.
Main Characteristics and Comparisons
Let’s compare VPN concentrators with similar networking terms:
| Characteristic | VPN Concentrator | Firewall | Router |
|---|---|---|---|
| Function | Secure remote access | Network security | Network connectivity and management |
| Encryption | Yes | Yes | No (Some models offer VPN support) |
| Authentication | Yes | Yes | No (Some models offer basic auth) |
| Scalability | High | Medium | High |
| Traffic Management | Yes | Yes | Yes |
Perspectives and Future Technologies
The future of VPN concentrators lies in:
- Software-Defined Networking (SDN): Leveraging SDN principles to enhance flexibility, scalability, and manageability.
- Integration with Cloud Services: Integrating VPN concentrators with cloud-based services to provide seamless connectivity and enhanced security.
- Advanced Encryption Techniques: Adoption of quantum-resistant encryption algorithms to future-proof VPN security.
VPN and VPN Concentrator
VPN concentrators work in tandem with VPN technologies to ensure secure and private communication over public networks. While VPNs encrypt and tunnel traffic, VPN concentrators manage and facilitate these connections, providing centralized access control and authentication.
Resources for Further Information
This comprehensive guide aims to elucidate the role, features, challenges, and future prospects of VPN concentrators in modern networking environments. Whether used for remote access, branch connectivity, or partner collaboration, VPN concentrators play a pivotal role in ensuring secure and reliable communication over the internet.