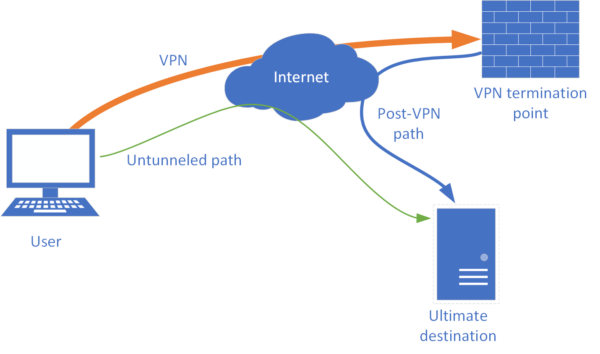
Brief Overview
A VPN tunnel is a secure pathway within an otherwise unsecured network, typically the internet, that allows for the transmission of data between two or more devices or networks in a private and encrypted manner. It is a crucial component of VPN (Virtual Private Network) technology, enabling users to establish secure connections over public networks.
Detailed Explanation
A VPN tunnel works by encapsulating data packets in layers of encryption, which are then transmitted over the internet. This encryption ensures that the data remains confidential and secure from unauthorized access or interception by malicious third parties. The tunneling protocol used, such as OpenVPN, IPSec, or WireGuard, dictates how the data is encapsulated and transmitted across the network.
Key Features Analysis
The key features of a VPN tunnel include:
- Encryption: Data transmitted through the tunnel is encrypted, ensuring confidentiality and privacy.
- Authentication: Users must authenticate themselves before accessing the VPN tunnel, adding an extra layer of security.
- Data Integrity: Mechanisms are in place to detect and prevent data tampering during transmission.
- Secure Protocols: VPN tunnels support various secure protocols for establishing and maintaining connections, such as SSL/TLS, IKEv2, and L2TP/IPSec.
Types of VPN Tunnels
There are several types of VPN tunnels, each with its own characteristics and use cases. Some common types include:
| Type | Description |
|---|---|
| Site-to-Site VPN | Connects multiple networks or sites together over the internet, allowing secure communication between them. |
| Remote Access VPN | Enables individual users to securely access a private network from a remote location, such as home or a public Wi-Fi hotspot, using a VPN client installed on their device. |
| Client-to-Site VPN | Similar to remote access VPN but typically refers to VPN connections established by individual clients to access a specific network or resource. |
Ways to Use VPN Tunnels
VPN tunnels are used for a variety of purposes, including:
- Securing Remote Access: Employees can securely access company resources from remote locations.
- Bypassing Geographical Restrictions: Users can access geo-blocked content by connecting to servers in different locations.
- Protecting Privacy: VPN tunnels encrypt internet traffic, protecting users’ privacy and anonymity online.
- Enhancing Security: VPN tunnels add an extra layer of security when using public Wi-Fi networks, protecting against potential threats such as hacking or data interception.
Challenges and Solutions
While VPN tunnels offer numerous benefits, they also present some challenges, such as:
- Slow Connection Speeds: Encryption and routing through the VPN tunnel can sometimes lead to slower internet speeds.
- Compatibility Issues: VPN tunnels may encounter compatibility issues with certain devices or applications.
- Security Risks: Vulnerabilities in VPN protocols or misconfigurations can pose security risks.
These challenges can be mitigated through measures such as optimizing VPN configurations, using reliable VPN protocols, and regularly updating VPN software to patch security vulnerabilities.
Characteristics and Comparisons
| Characteristic | VPN Tunnel | Similar Terms |
|---|---|---|
| Encryption Strength | Uses strong encryption algorithms to secure data | Similar to VPNs, but specifically refers to the secure pathway created |
| within the VPN for data transmission | ||
| Authentication Mechanisms | Supports various authentication methods for user | Similar to VPNs, but specifically refers to the secure pathway created |
| authentication | within the VPN for data transmission | |
| Protocol Support | Compatible with multiple tunneling protocols | Similar to VPNs, but specifically refers to the secure pathway created |
| within the VPN for data transmission |
Future Perspectives and Technologies
The future of VPN tunnels is likely to involve advancements in encryption algorithms, protocol enhancements for improved performance and security, and integration with emerging technologies such as blockchain and decentralized networks. Additionally, the widespread adoption of IPv6 and the increasing demand for secure remote access solutions are expected to drive further innovation in VPN tunneling technologies.
VPN Tunnel Association
VPN tunnels are closely associated with VPNs, as they form the secure pathway through which data is transmitted within the VPN network. Without VPN tunnels, the privacy, security, and functionality of VPNs would be compromised, making them an integral component of VPN technology.
Resources for Further Information
For more information about VPN tunnels, consider exploring the following resources:
- RFC 2637: Point-to-Point Tunneling Protocol (PPTP)
- RFC 4026: Encapsulating IPsec ESP in UDP for NAT Traversal
- OpenVPN Documentation
- WireGuard Documentation
This comprehensive guide provides insights into the workings, applications, challenges, and future prospects of VPN tunnels, essential for anyone seeking to understand this critical aspect of modern networking and cybersecurity.