Virtual Private Networks (VPNs) are a cornerstone of modern digital privacy and security, providing a crucial layer of encryption and anonymity for internet users worldwide. This guide delves into the intricacies of VPN technology, offering a deep dive into its functionality, benefits, types, and applications.
Understanding VPNs: A Primer
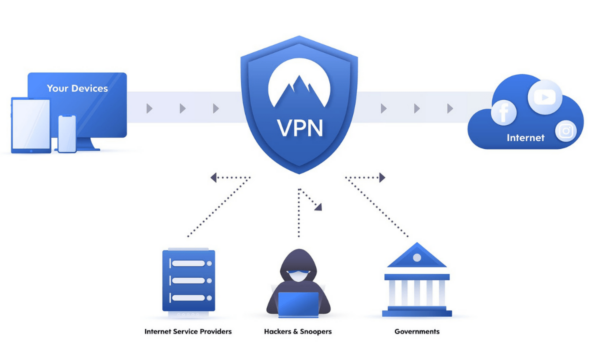
At its core, a VPN is a service that creates a secure, encrypted tunnel for your internet traffic, effectively shielding your data from prying eyes on public networks. By routing your connection through a VPN server, your IP address is masked, making your online actions much harder to track. This encryption helps protect your privacy and secure your data from cyber threats such as hacking, eavesdropping, and identity theft.
The Anatomy of VPN Technology
VPNs employ a combination of encryption protocols and dedicated connections to create a secure network over the internet. This section delves into the various components that make up a VPN, including:
- Encryption Protocols: The methods by which data is encrypted, such as OpenVPN, IKEv2, and WireGuard, each offering different levels of security and speed.
- Tunneling Protocols: The process of encapsulating data packets within another packet before transmission, including PPTP, L2TP/IPSec, and SSTP.
- VPN Servers: Remote servers located worldwide that users connect to in order to encrypt their internet traffic and mask their IP address.
Key Features of VPN Services
VPN services offer several key features aimed at enhancing online privacy, security, and accessibility:
- Data Encryption: Encrypts your internet traffic, protecting sensitive information from cybercriminals.
- IP Masking: Conceals your real IP address, making your online activities more anonymous.
- Geo-Spoofing: Allows you to appear as if you’re browsing from a different location, bypassing geo-restrictions.
- Secure Connections: Offers a safer way to connect to public Wi-Fi networks, reducing the risk of data theft.
Types of VPNs Explored
VPNs can be categorized based on their use case, architecture, and deployment method. Here’s a breakdown:
| Type | Description | Use Case |
|---|---|---|
| Personal VPN | Services provided by third-party providers for individual use. | Personal privacy and security. |
| Corporate VPN | Designed for organizations to provide remote access to a secure company network. | Business data protection. |
| Site-to-Site VPN | Connects entire networks to each other, often used to connect branch offices to a central office. | Corporate network expansion. |
| SSL VPN | Allows users to securely access a network from any browser. | Secure remote access without client software. |
Practical Applications of VPNs
VPNs are versatile tools with a range of applications, including but not limited to:
- Enhancing Online Privacy: Protecting users’ identities and activities from surveillance and tracking.
- Securing Public Wi-Fi Connections: Safeguarding data on insecure networks such as cafes and airports.
- Accessing Geo-Restricted Content: Streaming services, websites, and applications not available in the user’s country.
- Safe Remote Work: Enabling secure access to corporate networks for remote employees.
Challenges and Solutions in VPN Usage
While VPNs are powerful tools for online security, they are not without their challenges:
| Problem | Solution |
|---|---|
| Slow Connection Speed | Opt for a VPN with high-speed servers and modern protocols like WireGuard. |
| Blocked VPN Services | Use obfuscated servers designed to bypass VPN blocks and restrictions. |
| Privacy Concerns | Choose a no-logs VPN provider to ensure your data isn’t stored or shared. |
Comparative Analysis: VPN vs. Similar Technologies
| Feature | VPN | Proxy | Tor |
|---|---|---|---|
| Anonymity | High (IP masking) | Medium (IP masking, no encryption) | Very High (multi-layered encryption) |
| Encryption | Yes | No | Yes |
| Speed | Moderate to Fast | Fast | Slow |
| Ease of Use | User-friendly | User-friendly | Requires some technical knowledge |
The Future of VPN Technology
Emerging technologies and evolving cybersecurity threats are shaping the future of VPNs. Advancements in encryption protocols, such as the development of quantum-resistant algorithms, and the integration of VPN functionality into mainstream devices and operating systems, signal a future where secure, private internet access is more accessible and reliable than ever before.
Expanding the Utility of VPNs
Beyond traditional applications, VPNs are finding new uses in various fields, including:
- Enhanced Gaming: Reducing ping times and bypassing IP bans.
- **