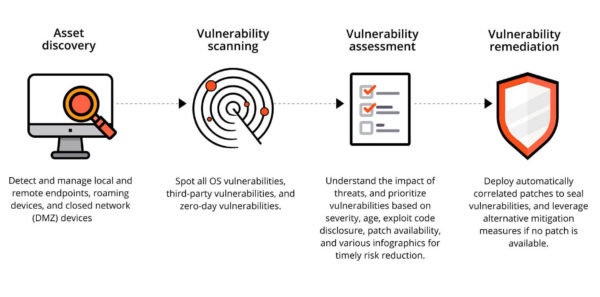
Vulnerability Assessment (VA) is a critical process in the realm of cybersecurity, focusing on identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. It involves a systematic review of security weaknesses in an information system and assesses the risk associated with those weaknesses. This process is essential for maintaining the integrity, confidentiality, and availability of data within an organization.
Understanding Vulnerability Assessment
Vulnerability Assessment is a cornerstone of cybersecurity strategies. It extends beyond mere identification of system vulnerabilities to include a detailed evaluation of potential threats and their possible impact on business operations. By employing automated tools and expert insights, VA aims to expose security flaws, outdated software, and unpatched systems, which could potentially be exploited by cybercriminals.
Key Features of Vulnerability Assessment
The effectiveness of Vulnerability Assessment lies in its comprehensive approach to security. Key features include:
- Automated Scanning: Automated tools are used to scan systems for known vulnerabilities, significantly speeding up the assessment process.
- Risk Analysis: Each identified vulnerability is evaluated to determine its potential impact on the system, allowing organizations to prioritize remediation efforts.
- Compliance Checks: Assessments often include checks for compliance with relevant regulations and standards, ensuring that organizations meet required security benchmarks.
- Reporting and Recommendations: Detailed reports outline found vulnerabilities and suggest corrective actions, providing a roadmap for strengthening system security.
Types of Vulnerability Assessment
The scope of Vulnerability Assessment can vary, leading to different types of assessments:
| Type | Description |
|---|---|
| Network-Based Scans | Identifies vulnerabilities in network devices, such as routers and switches. |
| Host-Based Scans | Examines operating systems and software applications for security issues. |
| Wireless Network Scans | Focuses on wireless network infrastructures to find security weaknesses. |
| Application Scans | Targets web applications to identify security flaws in coding and design. |
Applications of Vulnerability Assessment
Vulnerability Assessment serves multiple purposes across various sectors:
- Preventive Security: Identifying and addressing vulnerabilities before they can be exploited.
- Compliance: Ensuring systems adhere to security standards and regulations.
- Security Enhancements: Guiding the development and implementation of stronger security measures.
Challenges and Solutions in Vulnerability Assessment
While essential, Vulnerability Assessment faces several challenges:
- Volume of Vulnerabilities: The sheer number of vulnerabilities can be overwhelming. Solution: Prioritization based on risk helps focus on the most critical issues.
- False Positives: Incorrectly identifying normal activities as vulnerabilities. Solution: Combining automated tools with expert analysis can reduce false positives.
- Resource Constraints: Limited resources can hinder comprehensive assessments. Solution: Focused assessments and outsourcing can optimize resource usage.
Comparative Analysis with Similar Terms
| Term | Description |
|---|---|
| Vulnerability Assessment | Focuses on identifying and prioritizing vulnerabilities in a system. |
| Penetration Testing | Simulates cyber-attacks to test the resilience of systems against breaches. |
| Risk Assessment | Evaluates the potential impact of identified vulnerabilities on the business. |
Future Trends in Vulnerability Assessment
Emerging technologies and methodologies are shaping the future of Vulnerability Assessment, including:
- Machine Learning: Enhancing the accuracy of vulnerability detection and reducing false positives.
- Cloud-Based Assessments: Facilitating scalable and flexible assessment capabilities for cloud environments.
- Automated Patch Management: Streamlining the remediation process by automatically applying necessary patches.
The Role of VPN in Vulnerability Assessment
Virtual Private Networks (VPNs) can play a crucial role in the Vulnerability Assessment process:
- Secure Remote Access: VPNs provide secure access to internal networks for remote vulnerability assessments, ensuring data is encrypted and protected from interception.
- Anonymity in Testing: VPNs can help mask the origins of assessment activities, allowing testers to simulate external attacks more realistically.
Further Reading and Resources
For more in-depth information on Vulnerability Assessment, consider the following resources:
- National Institute of Standards and Technology (NIST)
- Open Web Application Security Project (OWASP)
- SANS Institute
This comprehensive overview of Vulnerability Assessment highlights its significance in enhancing organizational cybersecurity. By understanding and effectively implementing VA practices, organizations can significantly reduce their risk profile and protect against potential cyber threats.