Brief Information
A hash function is a fundamental cryptographic algorithm that takes an input (or “message”) and returns a fixed-size string of bytes. The output, known as the hash value or hash code, is typically a unique representation of the input data. Hash functions are widely used in various fields, including cryptography, data integrity verification, password storage, and digital signatures.
Detailed Information
Hash functions play a crucial role in modern cryptography and computing systems. They are designed to efficiently map data of arbitrary size to a fixed-size hash value. This ensures that even a small change in the input data results in a significantly different hash value, making hash functions suitable for tasks such as data integrity verification and digital signatures.
Key Features
- Deterministic: Given the same input, a hash function always produces the same output.
- Fast Computation: Hash functions are computationally efficient, allowing for quick processing of large datasets.
- Fixed Output Size: Hash functions produce output of a fixed length, regardless of the input size.
- Avalanche Effect: A small change in the input results in a significantly different hash value.
- Collision Resistance: It is computationally infeasible to find two different inputs that produce the same hash value.
Types of Hash Functions
Hash functions can be classified into various types based on their cryptographic properties and applications. Some common types include:
| Type | Description |
|---|---|
| Cryptographic Hash | Designed for use in cryptography, ensuring collision resistance |
| Non-Cryptographic | Primarily used for data integrity verification, not necessarily secure |
| Secure Hash | Provides strong collision resistance and pre-image resistance |
| Message Digest | Hash functions used in digital signatures and data integrity checking |
Ways to Use Hash Function
Hash functions have a wide range of applications across different domains:
- Data Integrity Verification: Hash functions are used to verify the integrity of data by generating a hash value for the original data and comparing it to the hash value calculated for the received data.
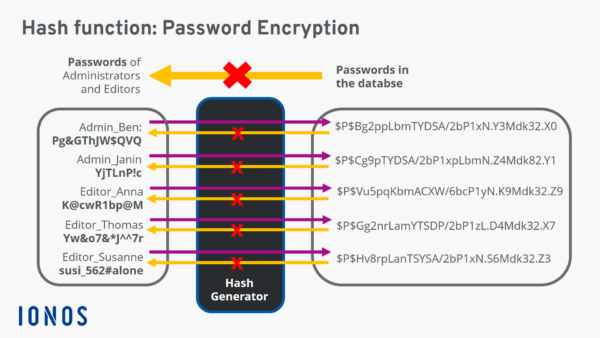
- Password Storage: Hash functions are utilized to securely store passwords by hashing them before storage. This ensures that even if the password database is compromised, the original passwords remain hidden.
- Digital Signatures: Hash functions play a crucial role in digital signatures by generating a unique hash value for a message, which is then encrypted using a private key to create a digital signature.
- Cryptographic Applications: Hash functions are integral to various cryptographic protocols, including HMAC (Hash-based Message Authentication Code) and key derivation functions.
Problems and Solutions
Despite their widespread use, hash functions are not without challenges:
- Collision Attacks: In certain scenarios, it may be possible for an attacker to find two different inputs that produce the same hash value, leading to a collision. This can compromise the integrity of data or cryptographic systems.
- Algorithm Weakness: Some hash functions may exhibit vulnerabilities to cryptographic attacks, necessitating the use of more secure algorithms.
- Hardware Limitations: Hardware implementations of hash functions may suffer from performance limitations or side-channel attacks.
To mitigate these challenges, ongoing research focuses on developing more robust hash functions with enhanced security properties and resistance to attacks. Regular updates and algorithm improvements are essential to address emerging threats and vulnerabilities.
Characteristics and Comparisons
| Characteristic | Hash Function | Similar Terms |
|---|---|---|
| Collision Resistance | High | Lower in non-cryptographic hashes |
| Pre-image Resistance | Strong | Not applicable in all cases |
| Speed | Fast computation | Varies depending on implementation |
| Output Size | Fixed | Variable |
Future Perspectives
The future of hash functions lies in the development of more secure algorithms and techniques to withstand increasingly sophisticated attacks. Emerging technologies such as quantum computing pose new challenges to traditional hash functions, necessitating the exploration of quantum-resistant alternatives.
VPN and Hash Functions
VPN services often utilize hash functions for various purposes, including:
- Data Integrity: Hash functions are used to verify the integrity of transmitted data, ensuring that it has not been tampered with during transit.
- Authentication: Hash functions play a role in VPN authentication protocols, helping to verify the identity of users and ensure secure connections.
- Key Management: Hash functions are employed in key derivation functions and cryptographic protocols used for key exchange in VPNs, enhancing security.
By incorporating hash functions into their protocols, VPN services can enhance the security and reliability of their networks, ensuring the confidentiality and integrity of users’ data.
Resources
For more information about hash functions, cryptographic protocols, and related topics, consider exploring the following resources:
- National Institute of Standards and Technology (NIST) – Cryptographic Hash Functions: Link
- Cryptography and Network Security by William Stallings
- Handbook of Applied Cryptography by Alfred J. Menezes, Paul C. van Oorschot, and Scott A. Vanstone