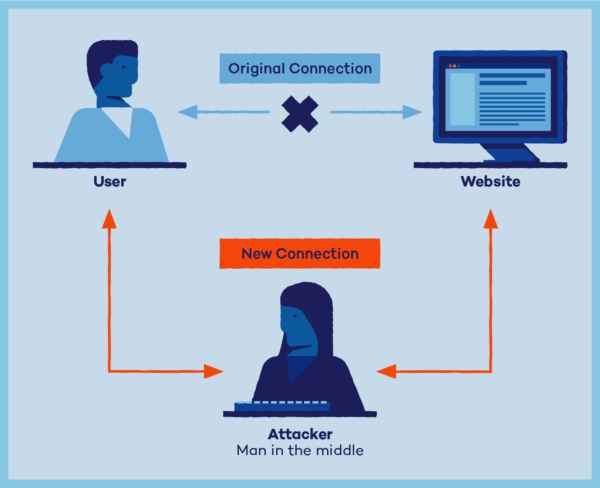
Brief Information about Man-in-the-Middle Attack:
A Man-in-the-Middle (MitM) attack is a cybersecurity threat where a malicious actor intercepts and possibly alters communication between two parties without their knowledge. This attack can occur in various forms, targeting both individuals and organizations, posing significant risks to confidentiality, integrity, and security.
Detailed Information about Man-in-the-Middle Attack:
A Man-in-the-Middle attack occurs when an attacker inserts themselves between the communication of two parties, intercepting and potentially altering the data transmitted between them. This attack can take place in both physical and digital environments, exploiting vulnerabilities in network protocols, software, or hardware. The attacker typically aims to eavesdrop on sensitive information or manipulate the communication for their benefit, such as stealing credentials, injecting malware, or altering transactions.
Detailed Analysis of the Key Features of Man-in-the-Middle Attack:
- Interception: The attacker intercepts communication between two parties, often without their knowledge.
- Modification: The attacker can modify the intercepted data to achieve their objectives, such as altering messages or redirecting traffic.
- Impersonation: In some cases, the attacker may impersonate one or both parties to gain further control over the communication.
- Stealth: MitM attacks can be difficult to detect, especially if the attacker employs sophisticated techniques to remain undetected.
Types of Man-in-the-Middle Attack:
Man-in-the-Middle attacks can manifest in several forms, including:
| Type | Description |
|---|---|
| Session Hijacking | Attacker takes control of an ongoing session between two parties, gaining unauthorized access to data. |
| SSL Stripping | Attacker downgrades a secure HTTPS connection to HTTP, allowing them to intercept unencrypted data. |
| DNS Spoofing | Attacker redirects DNS queries to a malicious server, leading users to unintended or fake websites. |
| Wi-Fi Eavesdropping | Attacker intercepts data transmitted over unsecured Wi-Fi networks, capturing sensitive information. |
| Email Hijacking | Attacker intercepts and alters email communication between sender and recipient, often for malicious purposes. |
Ways to Use Man-in-the-Middle Attack:
- Identity Theft: Stealing credentials, personal information, or financial data.
- Data Interception: Eavesdropping on sensitive communications for espionage or fraud.
- Tampering: Altering messages, transactions, or software updates to manipulate outcomes.
- Session Hijacking: Taking control of user sessions to impersonate legitimate users or gain unauthorized access.
Problems Arising with the Use of Man-in-the-Middle Attack and Solutions:
- Security Risks: MitM attacks compromise the confidentiality and integrity of data. Employing encryption, implementing secure protocols, and regularly updating software can mitigate these risks.
- Legal Concerns: Engaging in MitM attacks is illegal in many jurisdictions and can result in severe penalties. Educating users about cybersecurity best practices and enforcing strict security policies can help prevent such activities.
- Detection Challenges: MitM attacks can be challenging to detect, especially if the attacker remains stealthy. Implementing intrusion detection systems, conducting regular security audits, and monitoring network traffic can aid in identifying suspicious activities.
Main Characteristics and Comparisons with Similar Terms:
| Characteristic | Man-in-the-Middle Attack | Man-in-the-Browser Attack | Packet Sniffing |
|---|---|---|---|
| Method of Attack | Intercepting communication between two parties. | Targeting web browser vulnerabilities to manipulate web sessions. | Capturing data packets transmitted over a network. |
| Scope | Can target various communication channels and protocols. | Specific to web browser sessions. | Generalized interception of network traffic. |
| Objective | Eavesdropping, data manipulation, identity theft. | Stealing credentials, manipulating web sessions. | Capturing sensitive information, network analysis. |
Perspectives and Technologies of the Future Related to Man-in-the-Middle Attack:
- Advanced Encryption: Continued advancements in encryption algorithms and protocols can enhance data protection against MitM attacks.
- Behavioral Analysis: Implementing behavioral analysis techniques can help identify abnormal communication patterns indicative of MitM attacks.
- Machine Learning: Leveraging machine learning algorithms for anomaly detection and threat prediction can strengthen MitM attack detection capabilities.
How VPN Can Be Used or Associated with Man-in-the-Middle Attack:
While VPNs are primarily designed to enhance privacy and security by encrypting communication and masking IP addresses, they can inadvertently facilitate MitM attacks if not implemented correctly. VPNs can provide a secure tunnel for communication, protecting against interception by external attackers. However, if the VPN server itself is compromised or controlled by malicious actors, it could become a point of vulnerability susceptible to MitM attacks. Therefore, it’s essential to choose reputable VPN providers and regularly update VPN software to mitigate such risks.
Links to Resources for More Information about Man-in-the-Middle Attack:
- OWASP Man-in-the-Middle Attack
- MITRE ATT&CK for Man-in-the-Middle
- SANS Institute – Man-in-the-Middle Attacks
- NIST Special Publication 800-54 – Man-in-the-Middle Attack
This comprehensive guide provides insights into the nature, techniques, and mitigation strategies related to Man-in-the-Middle attacks, empowering users and organizations to safeguard their digital assets against this pervasive threat.